We’re aware the headline says “dummies”, but it’s essential you know we don’t mean it. There are just some topics some of us are content enough to go through life knowing nothing about and idly pretending we do and it has no bearing on whether or not we are, in fact, dummies. Like archipelagoes. We have no idea what an archipelago is. We don’t even know if we’re pronouncing it correctly. And that’s fine. We’re busy. We have to prioritize our brain space.
For many people, DDoS attacks have fallen into the same category that archipelagoes have for us. Something you hear about once in a while that sort of makes you think you should look into it but never quite do. Here’s the thing, though. If we were told archipelagoes do the kind of damage DDoS attacks do – namely, striking 45% of organizations and costing those organizations an average of $40,000 per hour – we’d get to reading up on archipelagoes posthaste.
And that’s why we give you this DDoS cheat sheet. What you need to know about what DDoS attacks are, how they strike, what kind of damage they do, and how to prevent them.
What a DDoS attack actually is
A DDoS attack is a Distributed Denial of Service attack. It’s an attempt to make a network, server, website or some other online resource unavailable to legitimate users by suspending or interrupting the services of a host that is connected to the internet. As you can imagine, DDoS attacks are always malicious.
The difference between DDoS and DoS
One letter. Ta-da. But since you understandably expect a little better from us, we’ll clarify that a DoS attack is a Denial of Service attack. Denial of Service attacks use one computer and one internet connection to flood a target with packets and overwhelm its resources, while Distributed Denial of Service attacks distribute the attack method by using many computers and internet connections to target a host and its resources.
Where all those computer and internet connections come from
The good news is that there isn’t some massive global army of people out there who are willing to let their computers and internet connections be used in DDoS attacks. The bad news is that the attackers behind DDoS attacks don’t really need computers and internet connections to be volunteered.
DDoS attacks are typically accomplished using what is referred to as a ‘Botnet.’ A Botnet is a number of computers that are 1) connected to the internet and 2) have been maliciously taken over, generally using malware like a Trojan Horse, and are being controlled by an external source through standard network protocols. The actual owners of the affected computers tend to not be aware of their membership in a Botnet’s so-called zombie army.
According to Incapsula’s 2014 bot traffic report, a stunning 29% of all visits to websites come from malicious bots.
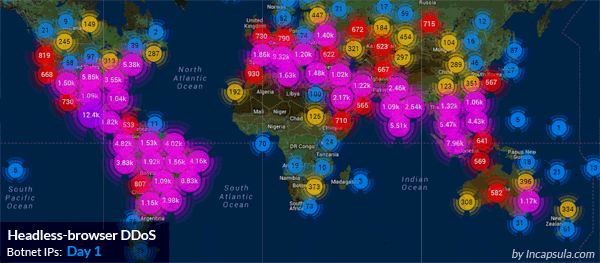
Demonstration of a massive HTTP flood: 690,000,000 DDoS requests from 180,000 botnets IPs
Common types of DDoS attacks
DDoS attacks can be generally divided into three categories:
- .Volume-based attacks. The goal of the volume-based DDoS attack is to saturate the bandwidth of the target, rendering that bandwidth unavailable to legitimate users. Volume-based attacks are most often accomplished through ‘floods,’ like UDP floods and ICMP floods, which occur when a host port on the target is flooded with packets – packages of data that are sent across the internet in order to accomplish pretty much everything we do on the internet. One of the most devastating types of volume-based attacks as well as one of the most widely-used is the NTP amplification attack.
- .Protocol attacks. These attacks are used to consume actual server resources or, alternately, the resources of intermediary communication equipment, including load balancers and firewalls. This can be accomplished through DDoS attack variants like SYN floods, where packet requests are sent from a spoofed IP address to a target host, rendering the target host unable to properly reply to the requests and leaving the target host with a bunch of open connections that bind resources. Another common type of protocol DDoS attack is called the Ping of Death, which is where an IP packet sent to the target host ends up being larger than the maximum packet size, overflowing memory buffers and causing legitimate packets to be turned away.
- .Application layer attacks. These are generally highly-targeted attacks that use either partial packet requests that can’t be replied to and leave connections open and unusable for legitimate packet requests, as in the case of the Slowloris attack, or seemingly legitimate HTTP GET or POST requests that force the server to allocate resources in response to each single request. This type of attack is called an HTTP flood (see example image above). Regardless of which strategy is used, the end result is usually a crashed web server.
DDoS damage
As mentioned, internet security firm Incapsula’s research regarding DDoS impact on organizations found that 45% of all organizations surveyed had experienced a DDoS attack in 2014, with the average cost of fighting an attack ringing up to a whopping $40,000 per hour. Still breathing? Good, because we’re not quite done yet. Not only do DDoS attacks lay a beating on an organization’s finances, but they’re also found to cause at least one of the following: software or hardware replacement, a reduction in revenue, a loss of consumer trust, customer data theft, financial theft, and theft of intellectual property. The shockwaves of a DDoS attack can be felt for months, even years.
Defending against DDoS attacks
The latest and greatest in DDoS mitigation and protection is undoubtedly cloud-based anti-DDoS services. With professional, cloud-based DDoS mitigation, in the face of an attack protective services will be activated immediately outside of your network. This means that all traffic will be redirected to the cloud, with only the filtered traffic of legitimate users ever reaching your website.
This is the most effective possible protection against all three main types of DDoS attacks. For volume-based attacks, a scrubbing server absorbs the multi-gigabytes of packets directed at the host before they ever reach the target. For protocol attacks, a mitigating protocol differentiates between legitimate traffic and malicious traffic, allowing only legitimate traffic through. And for application layer attacks, real-time monitoring of site visitor behavior blocks malicious bots and implements security challenges for unrecognized visitors.
So there you have it: a primer on the horror that is DDoS attacks, and what can be done to protect your organization. It’s not always easy to learn new things, but we’re all better for it. In that spirit, an archipelago is a cluster, chain or group of islands. Which should probably just be called a group of islands.